You probably don’t give it much thought, but your router is one of the most important gadgets in your home – without it there’s no wi-fi for your laptops, your phones, and all the other web-connected devices you’ve got set up.
Everything that comes in and goes out of your home network goes through the router. It’s like a checkpoint station on a border, with traffic flowing in and out. It needs to be well defended too, not just to keep unwanted visitors out, but to make sure no one’s set up a surveillance system at the border to spy on which cars are entering and leaving (that’s your browsing history, if you’re still following the analogy).
Poor router security through the ages
Considering the router is in charge of access to your home (or office) network, you would think security would be a top priority for manufacturers and users alike. But vulnerabilities just keep on appearing, and often go ignored.
A 2014 report found that 20 of Amazon’s top 25 best-selling routers for small business and home office use had security vulnerabilities that could be exploited – vulnerabilities that were publicly documented on the web in a third of those cases. In September this year, a security researcher exposed 10 serious vulnerabilities in a consumer router sold by D-Link.
Image: Screenshot
Only last month, a known form of malware was able to take charge of nearly 100,000 exposed ZyXEL routers for botnet-building purposes, thanks to weak default security configurations left in place by an Argentinian ISP. If you want to know just how bad the problem is, this page lists currently known bugs and vulnerabilities.
Then there’s KRACK, the fatal flaw in the wi-fi security protocol that the vast majority of routers are currently using — until your router manufacturer issues an update, it puts your home network under threat from anyone within range of it.
While it’s true that hackers won’t necessarily be lining up on your driveway to steal some of your bandwidth for a Netflix binge-watching session, with a combination of malware programs and badly secured router settings your network could be accessed remotely, enlisted as a soldier in a botnet army, or spied on by government agencies. If you want your home network and the devices that connect to it to be safe, it starts with your router.
How routers work
Technically speaking, a router connects all the devices in your home and provides access to a modem, which actually does the job of communicating with the wider web. These days though, many units have combined the functions of modems and routers into one box, and just kept the name router. They’re also sometimes called gateways, depending on who you’re buying or renting them from.
Routers deal in data packets, which are exactly what they sound like. All the 1s and 0s that make up your Facebook feed or your Skype call are packaged up into blocks for transmission, together with identifying markers, error checks, and address labels. It’s like a huge Amazon warehouse, with packets rushing in and out at superfast speeds, all addressed to somewhere on the web (going out) or a device in your house (coming in).

Image: Netgear
The router gets its name because it routes all this data to the right place, even if the kids are watching Netflix downstairs and you’re streaming Spotify in the bedroom. Keeping this data separate, and stopping one device from spying on another, deliberately or otherwise, are two of the key jobs that routers have to handle.
The better your router, the faster it can juggle all this data, and the more devices it can work with at the same time. But as we’ve mentioned, it also needs to be locked down in terms of the data that’s allowed to pass through and the users and devices that are given permission to send and receive that data.
Router security basics
On the most basic level, your router improves security by presenting one IP address to the world — kind of like your postal address for the internet — and handling the IP addresses for your individual devices itself. If the bad guys lurking on the web can only see a gate to an estate rather than all the separate houses within, it’s harder for them to do any damage… though, of course, very much still possible.
Your router offers up a basic firewall against unwelcome and unrequested traffic from the wilds of the internet, primarily through what’s known as NAT (Network Address Translation) routing and port filtering. The NAT routing is essentially what we’ve already mentioned: hiding the IP addresses of all your devices behind one single address.

Image: Linksys
Any packets of data that arrive at your router must have been specifically requested by your phone, your laptop, or another device — if not, they get blocked and discarded. NAT routing does this by checking where packets are requesting to get sent, and if they don’t have a valid address for one of your devices, they get dropped.
To put it another way, it’s like couriers (data packets) turning up at your office’s reception desk (your router). If the package was specifically requested, and they have got a name and contact details for someone in the building, they can be let through. If the package is just vaguely aimed at anyone who works there, or someone who the reception desk have never heard of, it gets stopped.

Image: Netgear
Port forwarding and security issues
This protection system put up by your router is all well and good from a security standpoint, but it can occasionally trip up, as you’ll know if you’ve tried to use an application or service that needs special privileges (connecting to a gaming server or torrenting network are good examples).
In an attempt to make life a little easier for applications and servers, we have what’s known as port forwarding: This relaxes the rules a bit, so genuine requests that come into different ports can be automatically rerouted to the right place. In theory, it means less of a headache when you’re doing stuff like accessing your home computer from your office, which would otherwise take a lot of manual router configuration.

Image: Netgear
One of the tools used to manage port forwarding is UPnP, or Universal Plug and Play, which is available on most modern routers. Again, the idea is to make it easier for games consoles and smart TVs and other devices to open ports and manage port forwarding without a lot of configuration, but all too often it’s being used by malware programs to turn off your router’s most important security measures.
Most experts now recommend turning off UPnP unless you specifically need it. Smart IoT devices are also notorious for using the protocol to leave themselves open to attack, which is why you should check and double-check that your devices aren’t interfering with your router’s operation in ways they shouldn’t be — see below for more on this.
Protecting the local network
Those are the key ways your router protects your home network from outside attack, but what about local devices? Here the main barrier against access is your router’s wi-fi password, stopping anyone and everyone from wandering past your home and logging on to your internet connection.
This most probably uses a protocol called WPA2 or Wireless Protected Access 2 (if your router is using the older WEP or WAP standards, upgrade to WPA2 as soon as you can). Recent security scares notwithstanding, at the moment, it’s the safest option your router has for keeping unwanted visitors off your local network.

Image: Netgear
Key to WPA2 is data encryption: Just as encryption protects the data on your iPhone, WPA2 uses it to scramble the data travelling to and from your router, so it’s garbled and nonsensical to anyone lurking in your driveway with a laptop. WPA2 uses AES encryption, which is used by the US government and just about everyone else worldwide.
Without the decryption key (your wi-fi password), devices can’t see what’s happening on the network and can’t browse the web through your router. In other words, they’re completely locked out. This kind of router protection can be circumvented with a lot of time and effort – by a brute-force check on all possible password combinations, for example – but it’s likely not something your neighbour is going to go to the trouble of doing.
Keeping your router secure
You can, if you want, just sit back and leave your home network security in the hands of your router, but we’d advise you to take a more proactive approach than that. In fact, you might consider upgrading your router first of all — the standard-issue boxes that ISPs dish out are so ubiquitous that they’re prime targets for hackers.
Firmware updates are important, though you wouldn’t know it from the lack of any auto-update facility on most router models: You can typically find new firmware from your ISP or the router manufacturer, if you dig around on their site, but don’t expect very many updates over the course of a router’s lifetime. Any patches that do appear will address security issues and are therefore well worth installing.
Image: Screenshot
It’s also a good idea to change the default username and password required to edit your router’s settings – these credentials are different to your WPA2 password and need to be entered when you log into your router device via a special IP address your ISP or the router manufacturer will have given you.
As many routers come with the same default username and password combination, anyone who’s on your network could easily get at settings for WPA2, port forwarding, UPnP and so on. However, they would need to already have access to the network, so this isn’t something someone can do without your wi-fi password or physical access to your router.
Image: Screenshot
Speaking of passwords, it’s also sensible to change your wi-fi password every once in a while. You’ll have the inconvenience of needing to reconnect all of your devices, but it’s an effective way of blocking out any people or devices that might have surreptitiously gained access without your knowledge — like the neighbour who popped ’round for a drink and noticed your wi-fi password on a sticker your router along the way.
If your router has any remote management features, meanwhile, switch them off unless you know you’re going to be using them. By and large they should be safe to use, but they give hackers more ways to try and break through your router’s defences and should be left disabled for most of the time.
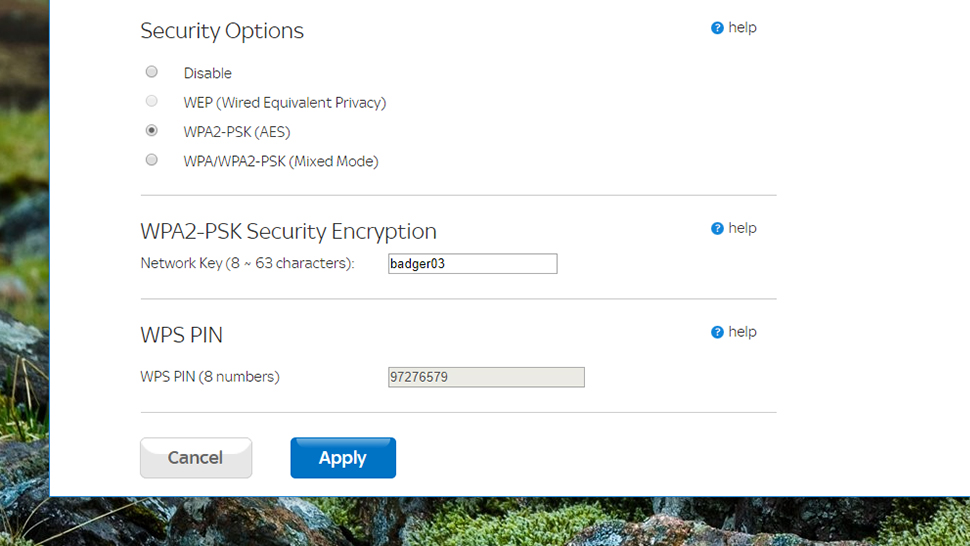
Image: Screenshot
Finally it’s a good idea to turn off WPS or Wi-Fi Protected Setup. The feature is designed to make it easier to connect new devices, with an 8-digit PIN or a button push, but of course that also makes it easier to get unauthorised access too — running a brute force attack on a PIN is much quicker than running one on a longer, alphanumerical password, especially when the last one is a checksum (in total there are around 11,000 combinations).
Some router manufacturers have shored up WPS security in recent years – by limiting the number of failed PIN attempts that can be made, for instance — but if you can find these options in your router’s settings, it’s still a good idea to switch off PIN access at least. The push-button method is relatively secure, as long as you trust the people who are coming in and out of your home.
This story was produced with support from the Mozilla Foundation as part of its mission to educate individuals about their security and privacy on the internet.